update
Showing
.helmignore
0 → 100644
Deploy.md
0 → 100644
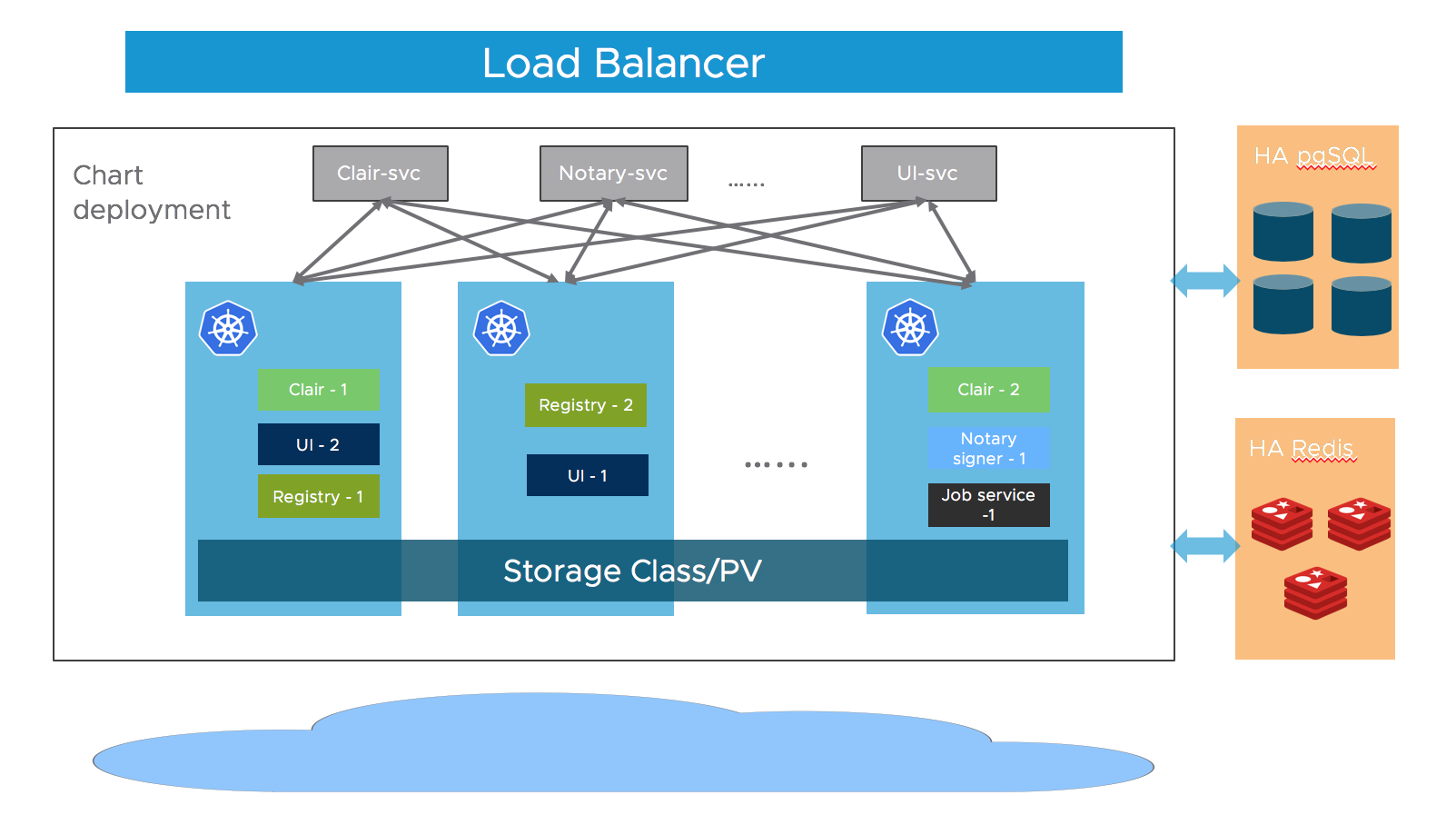
docs/High Availability.md
0 → 100644
docs/Upgrade.md
0 → 100644
docs/img/ha.png
0 → 100644
152 KB
logo.png
deleted
100644 → 0
61 KB
package.json
deleted
100644 → 0
templates/nginx/service.yaml
0 → 100644