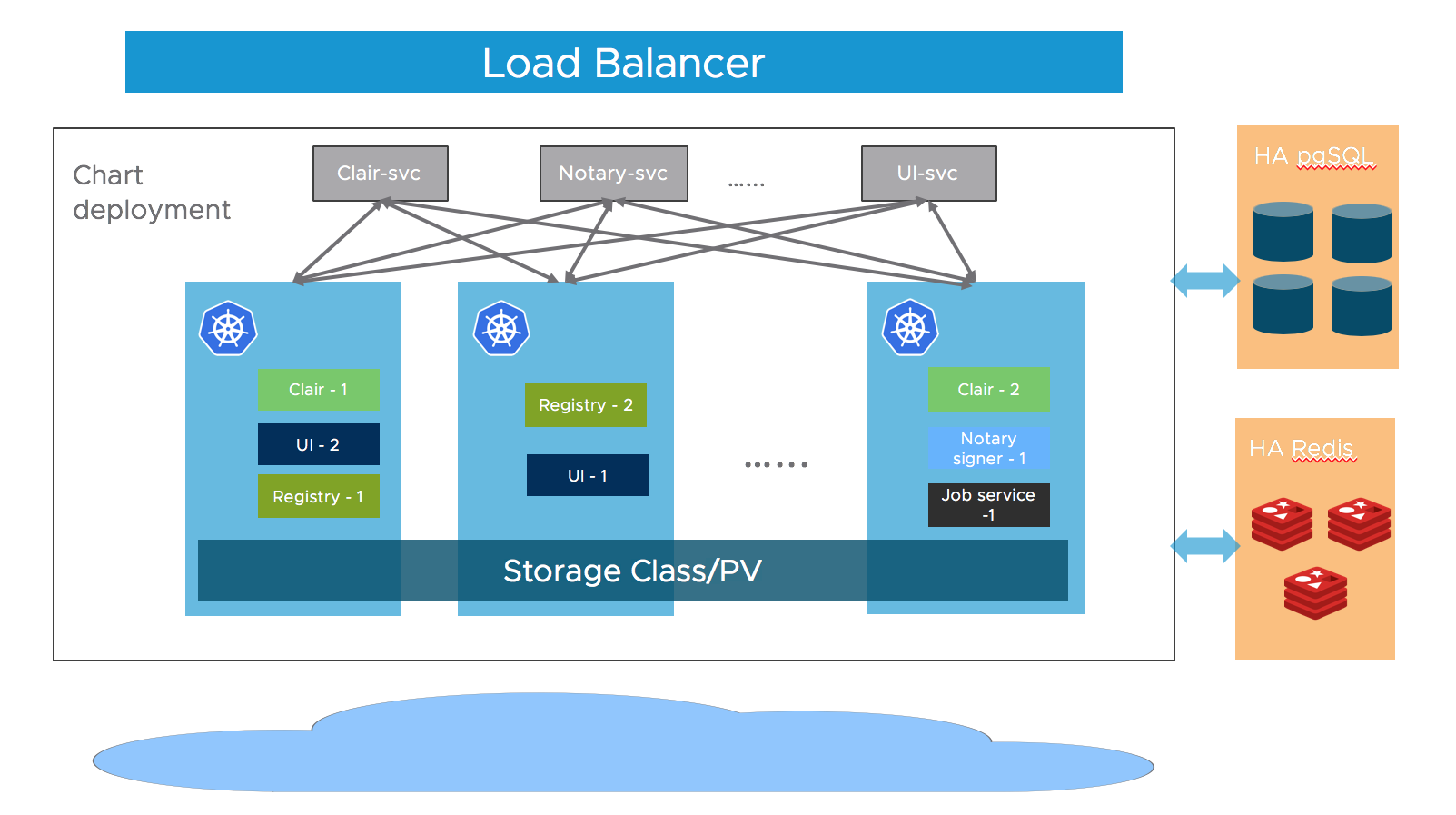
2.13.2
Showing
This source diff could not be displayed because it is too large. You can view the blob instead.
ansible/images.yaml
deleted
100644 → 0
cert/tls.crt
deleted
100644 → 0
cert/tls.key
deleted
100644 → 0
conf/clair.yaml
deleted
100644 → 0
docs/Upgrade.md
deleted
100644 → 0
docs/_index.md
deleted
100644 → 0
docs/img/ha.png
deleted
100644 → 0
152 KB
raws/values-arm.yaml
deleted
100644 → 0
raws/values-pg.yaml
deleted
100644 → 0
raws/values.yaml
deleted
100644 → 0
test/go.mod
deleted
100644 → 0
test/go.sum
deleted
100644 → 0
test/install_helm.sh
deleted
100644 → 0
test/test.go
deleted
100644 → 0
test/verify.sh
deleted
100644 → 0